Token-based Loyalty Program
Tokenization has revolutionized mobile and online payments. When you add a payment card to your mobile device or Amazon account, the card information is not saved on the mobile device or Amazon’s servers. Instead, a random string of characters called a token, is saved on the device or server while the card information is stored in a secure vault operated by a token service provider (TSP) and mapped to the token. If your mobile device gets stolen or your Amazon account gets hacked, the payment card information is protected because it was never stored on the device or server. When you initiate payment via your mobile device or Amazon account, the transaction details are forwarded to a TSP, which retrieves your card information and provides it to your payment card processor, such as Visa or MasterCard. Thereafter, the journey of your payment card transaction is similar to a transaction without involving tokens. The processor sends an authorization request to your payment card issuer. If the issuer approves the transaction, the processor sends the approval message to the acquiring bank, and the transaction is completed.
Payment card tokens were first introduced in the early 2000s as part of an industry-wide effort to enhance the security of digital payments. However, they became popular only around 2014 when industry leaders like Apple, Google, and Amazon adopted tokenization as a standard security measure for payment card transactions.
What is a Loyalty Program
A merchant loyalty program is a marketing strategy designed to encourage customers to continue making purchases from a retail store or partner network. The program rewards customers for repeat purchases through points, discounts, cashback, or other incentives. Merchant loyalty programs can be broadly classified as card-based or ID-based. To enroll in a card-based loyalty program, you must acquire a merchant loyalty card, which is also bundled with credit nowadays. The merchant loyalty card is analogous to any payment card and can be used outside the merchant’s establishment, too. You become eligible to receive a merchant loyalty card after the merchant has established your credentials. This means you must provide copies of two pieces of your official ID (passport, driving license, social security, health card) to the merchant. To enroll in an ID-based loyalty program, you must share your email ID or cellphone number with the merchant.
Both card-based and ID-based methods allow the merchant to track the spending behavior of the customer and reward him/her for their purchases. When a customer makes a purchase through the merchant-specific loyalty card, the payment cube can read the customer information embedded in the loyalty card. Once the customer information is obtained, the merchant’s POS terminal records the customer transaction in the customer’s account of the Merchant Loyalty Program database. Alternatively, if a customer makes a purchase using cash, he/she provides the merchant with their email address and/or cell phone number. The merchant types the customer information in their POS terminal and records the transaction record in the customer’s account of the Merchant Loyalty Program database.
Data Protection Issues in Loyalty Programs
The customer information acquired through the existing loyalty programs is highly vulnerable to data breaches. Retail merchants often work with credit reporting companies (CRAs) to collect and aggregate customer information sourced through merchant loyalty programs. This data is then used to generate credit reports and credit scores, which lenders and financial institutions use to assess an individual’s or business’s credibility. In the United States, there are three major CRAs: Equifax, Experian, and TransUnion. Equifax suffered a major data breach in 2017 in which the private records of 147.9 million Americans, along with 15.2 million British citizens and about 19,000 Canadian citizens, were compromised. The information accessed in the breach included first and last names, social security numbers, birth dates, addresses, and in some instances, driver’s license numbers for an estimated 143 million Americans. It is estimated that the breach cost Equifax over $1.7 billion in direct and indirect costs, including legal settlements, regulatory fines, customer compensation, security upgrades, and reputational damage.
What is a Token-based Loyalty Program
Although payment card tokens were invented to improve the security of online transactions, the underlying technology can have multiple use cases. The Token-based Loyalty Program (US12125054B2) repurposes the tokenization standard for running a merchant loyalty program that will allow payment cardholders to participate in unlimited merchant loyalty programs without acquiring additional loyalty cards or sharing their email ID/cellphone number. Customers don’t purchase goods and services from only one vendor, even if the vendor can provide all the goods and services the customer wants. Customers purchase goods and services from multiple vendors who compete with each other. If the customer acquires a loyalty card from each of these vendors, it creates problems for the customer as well as the vendor.
The first problem is that when a customer shares their private and confidential information with the merchant, there is a risk that the information might get into the wrong hands. Additionally, the customer has to accept the burden of managing another card. The second problem is that a card-based loyalty program provides a merchant with very limited visibility of the purchasing habits of the customer. For instance, a customer who has acquired a Starbucks loyalty card only provides information about their purchases at Starbucks. The same customer might be visiting many different eating places, such as Barista, Pizza Hut, and McDonalds, and the customer spending at these places would be of interest to Starbucks in order to diversify their menu. However, since this spending is hidden from Starbucks, it can only speculate about the customers’ eating choices.
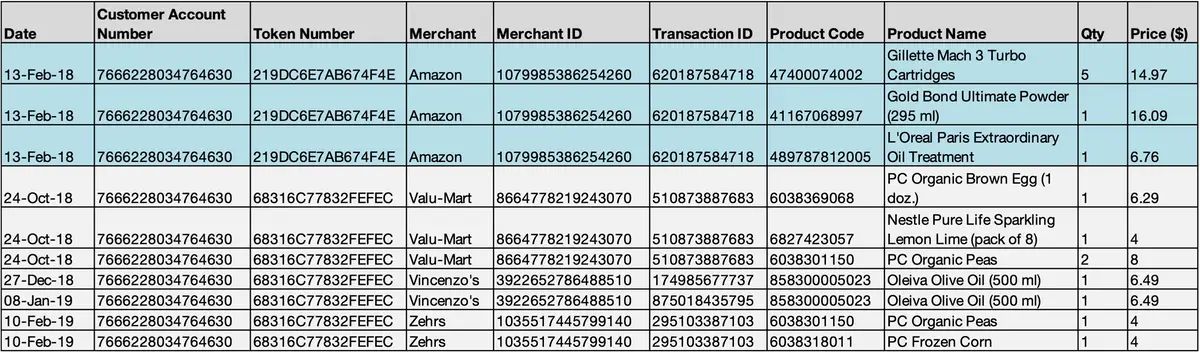
The digital infrastructure for token-based loyalty programs allows customers to create personal accounts on a server platform on the cloud and save all transaction records anonymously into their accounts. In the following table, a customer has anonymously captured his transaction records at multiple vendors into his online account. The customer can profit from this information by sharing it with a merchant who wants to understand the customer’s purchasing behavior and optimize their marketing and supply chain.
How Token-based Loyalty Program Works
Tokenization allows both merchants and customers to benefit from the security and reliability of the digital infrastructure supporting payment card tokens. The token-based loyalty program uses tokens to link a customer transaction record with the payment card used for the transaction. This invention is brand new and has never been used anywhere in the world. ValiDeck has filed a patent for this invention in six jurisdictions — Canada, USA, Europe, India, China, and Australia — and received an allowance for the invention in the USA and Australia.
To understand how the token-based loyalty program works, imagine a customer named Alice who wants to enroll herself in the Ardus merchant loyalty program. Ardus is a fictitious boutique design shop that sells home-use products, such as bed sheets, table linen, curtains, and sofa upholstery. Ardus has deployed a customized point of sale (POS) at its store that allows its customers to save their transaction records anonymously into a server database on the cloud. Customers can purchase products from Ardus by physically visiting their store or online. The customized POS is part of the token-based loyalty program solution.
Alice uses the following steps to enroll herself in the Ardus Merchant Loyalty Program and earn rewards for her transactions at Ardus and other merchants using the token-based loyalty program infrastructure developed by ValiDeck.
1. Registration
Alice creates an account on the ValiDeck platform by requesting a Unique ID (UID) through her bank, which already has a copy of her passport and driving license. The UID is different from any existing ID (passport number, driving license number, social security number) so as not to disclose her identity to the ValiDeck platform. Alice is, therefore, totally anonymous to ValiDeck.
2. Tokenizing
- Alice requests her payment card issuer to tokenize her payment card.
- The card issuing bank tokenizes the payment card and encrypts the token with the ValiDeck public key. The token is then stored in the issuer database as a Key:Value pair with the matching card number.
- The card issuing bank sends the encrypted token to ValiDeck. The tokens can be decrypted only via the matching private key available on the ValiDeck platform.
- ValiDeck decrypts the token and stores it in a queue. It then notifies the issuer, which informs Alice that the token is available for registration.
- Alice registers the token into her personal account on the ValiDeck platform.
3. Linking
- Alice purchases some products at Ardus and initiates a payment at their store.
- The Ardus point of sale (POS) requests their acquiring bank to authorize the transaction and the token number linked to the card. The acquiring bank forwards this request to the payment network, which subsequently passes it to the payment card issuer.
- The card issuing bank checks Alice’s bank account balance and authorizes the transaction. The authorization and the linked token number are sent to the payment network, which forwards them to the acquiring bank. The token number is encrypted with the ValiDeck public key.
- The Ardus POS receives the transaction authorization and the token number from the acquiring bank. The transaction record is linked with the token number via an API call and transmitted to the ValiDeck platform.
- The ValiDeck system decrypts the token number and looks up Alice’s account containing the token number. Once Alice’s account is found, the transaction record is written into the ValiDeck database and linked to Alice’s account number.
4. Earning Rewards
Alice receives reward points from Ardus for her purchases at the store and for sharing her transaction history at other home-use stores, such as Bed Bath and Beyond, Kohl’s, and Williams-Sonoma. Alice’s transaction records help Ardus optimize its marketing and supply chain operations.
Benefits of the Token-based Loyalty Program
The token-based loyalty program is an unparalleled opportunity to develop a self-service ecosystem for customers, businesses, and payment channels. The ecosystem will allow customers to join unlimited merchant loyalty programs without disclosing their personal and confidential information. In addition, the customers will be able to search for products, businesses, and services that they can trust and profit from their anonymous transaction records. The ecosystem will allow merchants to run a powerful loyalty program with just a payment cube and an Internet-ready terminal. Merchants will be able to understand customers’ purchasing behavior by collecting explicit and implicit reviews from them. In addition, the merchants will be able to optimize their marketing, sales, and distribution processes. The ecosystem will allow payment channels to significantly increase their revenues from higher usage of payment cards. Additionally, the payment channels will be able to generate new revenues through professional services, such as market insights and data analytics.